One of the challenges of running an application at the edge is to be able to access it the same way as any other application running in the normal hosting environments. In this blog post we will show you how to use DDNS client with [DuckDNS]https://www.duckdns.org/) to expose your application to the outside world! Let’s get started!
Important: This will not work if your devices are not able to be accessed via an external IP address. For this to work you might need to configure your router with a port forwarding. Which is out of scope for this blog post.
###Technologies used
- Synpse for hosting and running applications anywhere
- DDNS for managing DNS records for multiple DNS providers
- Let’s Encrypt for TLS certificates
- DuckDNS for alternative if you don’t onw a domain
###Domain
If you don’t onw a domain, and don’t have a need for it - you can use DuckDNS to get one for you. It is very convenient online service to get free, not malware based DNS name
Sign-in into DuckDNS and create a domain for your application.
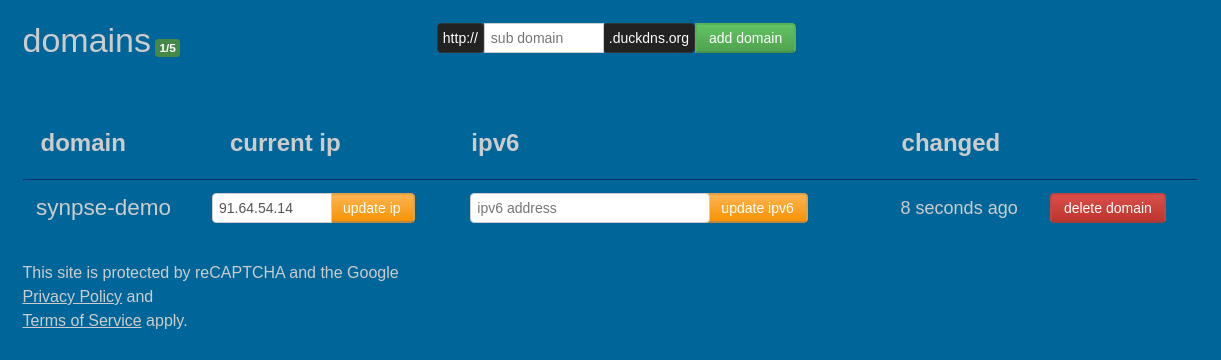
we go ourselfs a synpse-demo.duckdns.org
###Deploy basic application
As for an application, we will use quay.io/synpse/hello-synpse-go “Hello World” application.
We are going to deploy the it alone for now:
As a yaml:
|
|
We can access the application on our local network, but this is not our final goal:
|
|
###Extend an application with DDNS
We are going to use linuxserver docker image for DDNS client.
####Create DDNS config for DuckDNS
|
|
Our example config looks like this:
|
|
|
|
Extend “Hello world” application with DDNS image:
|
|
Once these steps are done, we should have:
- Application deployed and exposed on port 8080 http://synpse-demo.duckdns.org:8080
- DDNS running and managing DuckDNS configuration.
We could stop here, as this shows already how to expose an application.
But we will do one more step, add TLS certificate. For this, we will add “Let’s Encrypt” container to the mix and we will use CertBot
###Let’s Encrypt with DuckDNS
Let’s create a configuration for “CertBot” (same credentials as in DDNS). We gonna use them from the script, because all script is treated as a secret in Synpse. This script will renew the certificate on a periodic basis as certbot is not able to run as a daemon, which is required for containers:
|
|
|
|
and extend our existing application. Note variables we added to the original application and change of port.
|
|
Once the application is updated, rolled out and all components are running you should be able to see this:
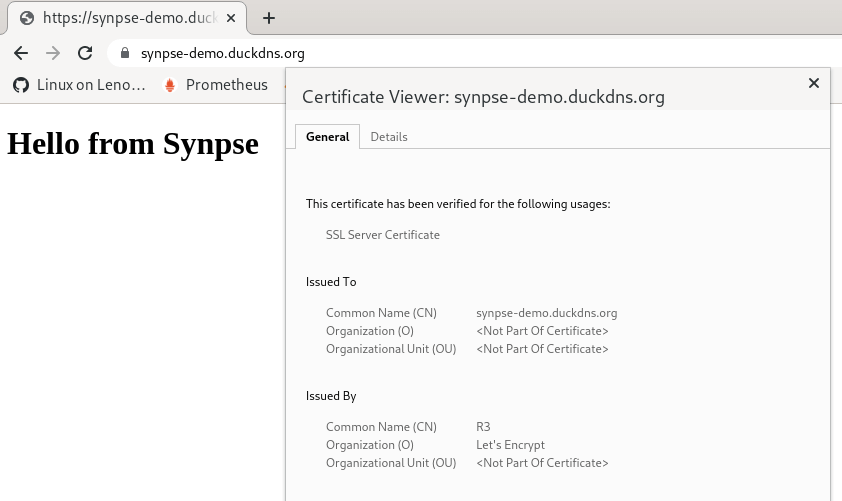
./wrap_up.sh
This stack now gives us a device at the edge, with TLS certificates from “Let’s Encrypt” with dynamic refresh and dynamic DNS updates for “DuckDNS”! This can be used for any other applications like “Drone”, “Prometheus”, “Grafana”. We will use this pattern in the future to show how you can deploy other applications!
In the next blog post we will show how you can use similar stack to expose application with your owned customer domain!
If you have any questions or suggestions, feel free to start a new discussion in our forum or drop us a line on Discord